SSH keys provide secure authentication for logging into SSH servers instead of using passwords. This guide covers generating SSH keys on Ubuntu 22.04, 20.04, or Debian, including converting to PEM, PPK, PUB formats. Using SSH keys adds an extra layer of security, even if your password is compromised.
Ubuntu 22.04/20.04/Linux: The Definitive Guide to SSH Key Creation

Step 1. Install PuTTY Tools & OpenSSH to Set Up SSH Key Authentication
PuTTY provides a secure remote connection to another server using the SSH (Secure Shell) protocol. It supports the setup of encryption algorithms such as (3DES, Arcfour, Blowfish, DES) and generates security keys, including a public key for authentication purposes. To install the putty-tools package, run the following command:
sudo apt update && sudo apt upgrade sudo apt install putty-tools
Install OpenSSH if not already, if it already exists then skip it.
sudo apt install openssh-server sudo systemctl start ssh sudo systemctl enable ssh
Step 2. Generate SSH Keys to authenticate the connection to the server
For Ubuntu and other Linux distributions, the generated SSH keys typically have the (.pub) extension for the public key and no extension for the private key. The private key can also be converted to the (.pem) format. The following command will generate the default SSH key pair on Ubuntu 22.04, 20.04, or Debian:
puttygen -t rsa -b 2048 -C "user@ip" -o keyfile.ppk
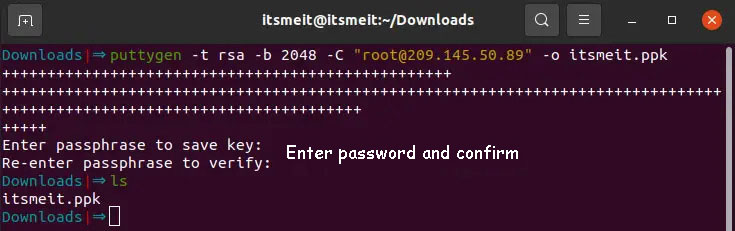
- The user here can use root or a username that exists on your server.
- The IP address is used to connect to the server. If you have resolved the domain name to an IP, the domain name can also be used for the connection.
- Set up a password with uppercase, lowercase letters, and number
Step 3. Generate Authorized Key for SSH Server Authentication
Method 1: Copy SSH Key Content to Server
After generate SSH keys for Linux/Ubuntu, you have received the “keyfile.ppk” file. The next step is to connect to the server as the root user and copy the contents of the keyfile.ppk into the authorized keys file located within the “.ssh” directory.
puttygen -L itsmeit.ppk | ssh root@ip "mkdir -p ~/.ssh && touch ~/.ssh/authorized_keys && chmod -R go= ~/.ssh && cat >> ~/.ssh/authorized_keys"
In the preceding command, “itsmeit.ppk” is the file name, and the terminal command is executed from the directory containing it, so the exact path to the file is not required. However, if you want to specify the exact path to the keyfile, you can do so, and then enter the password of the root user to establish a connection to the server.
Recommend:
- For the root user, the .ssh directory should be placed in the /root directory because after connecting to the server the root user will be moved to /root.
- For regular users, you can specify the desired directory to navigate to upon successful connection to the server. For instance, you may place the “.ssh” directory within the “/var/www/” directory for convenient management of a project.
Method 2. Manually Copying SSH Key Content to the Server
The second method is to manually copy the content to the server for SSH key authentication. After completing the steps to generate SSH keys on your Ubuntu or Debian, now you can connect to the server via SSH using the following command: ssh root@ip
ssh root@ip
Once you have connected, it is important to verify the existence of the ~/.ssh directory. If it does not exist, you will need to create it.
mkdir -p ~/.ssh
The following command can be executed in the terminal from the directory containing the created key file to retrieve the key file:
puttygen -L keyfile.ppk
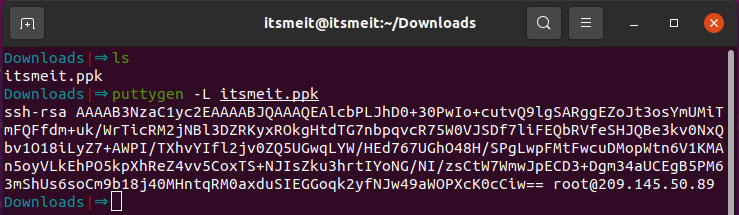
To complete the setup, create the authorized_keys file located in the .ssh directory and paste the contents of the “keyfile” into it. After making the necessary changes, save the file by pressing “Ctrl + X” and confirming with “Y”.
nano ~/.ssh/authorized_keys
Or use the echo command to add key.
echo ssh_key >> ~/.ssh/authorized_keys
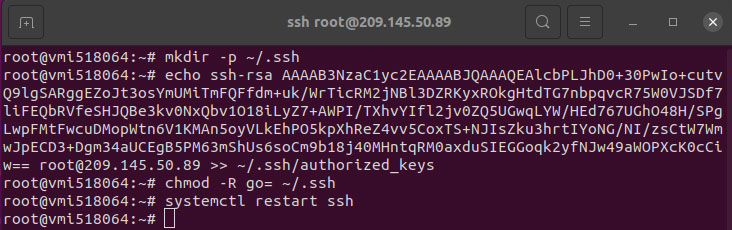
To authorize the .ssh folder, you need to change its permissions to secure it. You can do this by running the following command in the terminal:
chmod -R go= ~/.ssh
If you are using the root account to set up SSH keys for a regular user, it is important that the ~/.ssh directory permission belongs to that user. Replace user:group with user and group on your system.
chown -R user:group ~/.ssh
Finally, reset ssh.
systemctl restart ssh
Step 4. Connect to the server using SSH keys
On your Ubuntu computer, run the command to convert the generated PPK file to PEM, and when prompted, enter the password for the file.
puttygen /path/keyfile.ppk -O private-openssh -o /path/keyfile.pem
To ensure the security of the “keyfile.pem,” it is important to set its permissions to 600. This can be accomplished by running the following command:
sudo chmod -R 600 keyfile.pem
By setting the permissions to 600, you are making the file readable and writable only to the owner (you), and not to others. This helps to protect the confidentiality of the key and prevent unauthorized access to your server.
To connect to the server with the keyfile, on the terminal run the command: “ssh -i [keyfile].pem [user]@[server_ip_address]”
ssh -i /path/keyfile.pem user@ip
Step 5. Disable password authentication SSH on your server
Ensure that the connection to the server has been established using the generated SSH Keys and that you have maintained the highest level of access privileges (root) on the server. This will disable password-based SSH logins and allow access only through the “keyfile”. It is crucial to securely store the “keyfile” and remember the associated password.
After successfully generate SSH Keys on Ubuntu 22.04 | 20.04 or Linux and connecting to the server, you may wish to disable password authentication and only use the “keyfile“. In this scenario, we will guide you on how to edit the ssh configuration file, “sshd_config,” as follows:
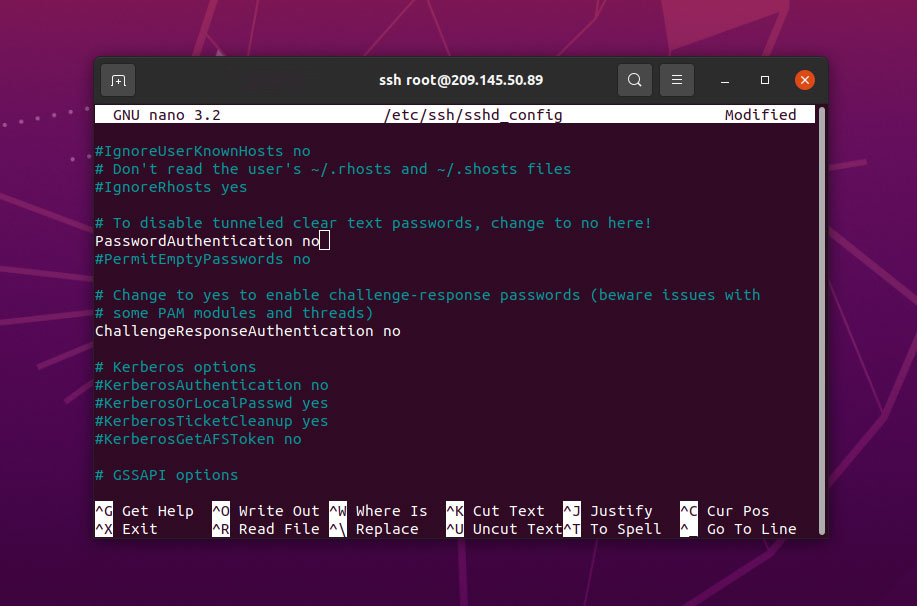
sudo nano /etc/ssh/sshd_config
Search for the line labeled “PasswordAuthentication” in the ssh configuration file, remove the leading # symbol to uncomment the line, and set its value to “no.” This action will prevent the possibility of logging into the server using your account password through SSH.
After making the necessary modifications to the ssh configuration file, save and close the file by pressing CTRL + X, confirming the save by pressing Y, and finally exiting nano by pressing ENTER. Finally, reset the ssh service to apply the changes.
Essential SSH Key Management and Usage Commands
- SSH Keys password change command
puttygen keyfile.ppk -P
- Convert key file command
puttygen keyfile.ppk -O private-openssh -o keyfile
You can convert your keyfile to various formats such as PPK, PUB, or PEM. It is important to back up your SSH Keys in a secure location and remember the password used to access them.
The steps outlined above provide a guide on how to generate SSH keys on Ubuntu 22.04, 20.04 & Linux, aimed at enhancing the security of your login to the server. If you have any questions or concerns, please don’t hesitate to leave a comment below.